Telephony Fraud – Still going strong

Who would believe, in the age of Skype, Whatsapp and Facebook – telephony fraud, one of the most lucrative and cleanest form of theft – is still going strong. Applications of the social nature are believed to be harming the world wide carrier market – and carrier are surely complaining to regulators – and for […]
Where will Asterisk be in your future?

A dear friend, the CEO of fone.do, Mr. Moshe Meir had written a blog post on the fone.do blog. The title is: “Is there a future for Asterisk?”
I have a different take on the thing. I think that Moshe is simply asking the wrong question. He should be asking “What is the role of Asterisk in your future?”.
Don’t Replicate – Federate
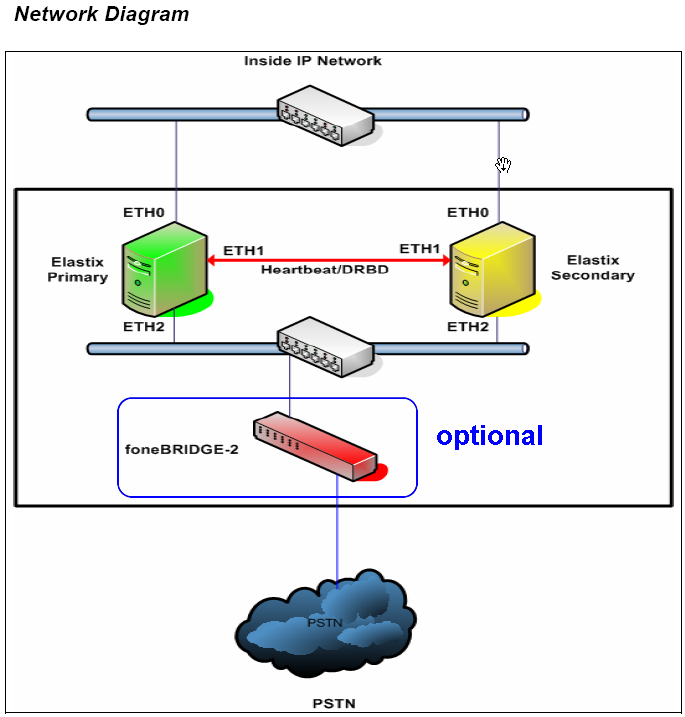
For many years, the question of high availability had always circled the same old subject of replication – how do we replicate data across nodes? how do we replicate the configuration to stay unified across nodes? Is active-active truly better than active-passive? and most importantly, what happens beyond the two node scenario?